A sophisticated attack by Russian-language actors is using a novel loader and malware-laced PNG image file to drop malware for stealing cryptocurrency or business account information, researchers said. The multistage campaign appears to be primarily targeting entities in Europe, the United States, and Latin America, Kaspersky researchers wrote in a blog post published June 12.
The attack begins with “DoubleFinger,” a multistage loader that drops a image file containing malicious code onto a victim’s computer. The malware infects victims with “GreetingGhoul,” a novel stealer specially designed to siphon off cryptocurrency credentials.
However, DoubleFinger isn’t exclusive to cryptocurrency attacks, the Kaspersky researchers said, as researchers also observed it dropping Remcos RAT, a popular tool among financially motivated cybercriminals. Once the Remcos RAT gets into an enterprise network, stopping the malware and its follow-on attacks can be difficult for businesses.
Russian-speaking artifacts within the code suggest that the perpetrators of this campaign come from a Commonwealth of Independent States nation, though the researchers qualified that “the pieces of Russian text and the victimology are not enough to conclude that the ones behind this campaign are indeed from the post-Soviet space.”
Stenography for Cryptocurrency
DoubleFinger attacks begin with a phishing email. If the victim clicks on the associated malicious program information file (.pif). This triggers a chain reaction leading to some malicious shellcode downloading a PNG image from imgur.com. The seemingly nondescript image utilizes steganography — hiding secret information within nonsecret data. The shellcode searches the PNG for a particular string in its code, 0xea79a5c6, which contains an encrypted payload.
The PNG with embedded shellcode. Source: Kaspersky
At the end of this attack chain, more often than not, is GreetingGhoul, an infostealer with two primary functions: It can detect victims’ cryptocurrency wallet apps and steal the sensitive credentials associated with them. GreenGhoul uses MS WebView2 — a tool for embedding web code into desktop apps — to overlay phishing pages on top of legitimate crypto-wallet interfaces. It’s a move that evokes banking Trojans of old, as users unwittingly type their sensitive wallet credentials into attacker-controlled fields.
The image below, for example, depicts an overlay mimicking Ledger, the world’s most popular vendor for cryptocurrency hardware wallets. It prompts victims to enter their wallet’s seed phrase — the ultrasensitive set of 12 or 24 words which generates their private key, and grants unfettered access to all contents of the wallet. This is why cryptocurrency investors are regularly reminded to never give up their seed phrases to access their wallets to anyone.
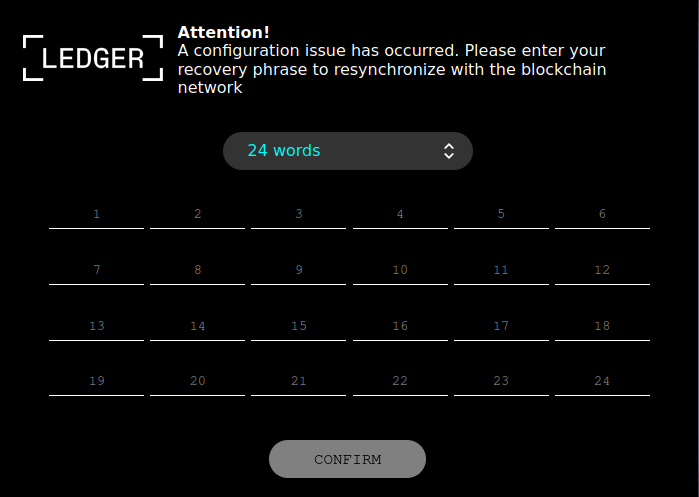
Source: Kaspersky






