
The findings of the 2023 Threat Landscape report of the European Union Agency for Cybersecurity (ENISA) highlights need for vigilance ahead of the upcoming European elections in 2024.
ENISA recorded approximately 2580 incidents during the reporting period starting from July 2022 up to June 2023. To this total, 220 incidents specifically targeting two or more EU Member States must be added.
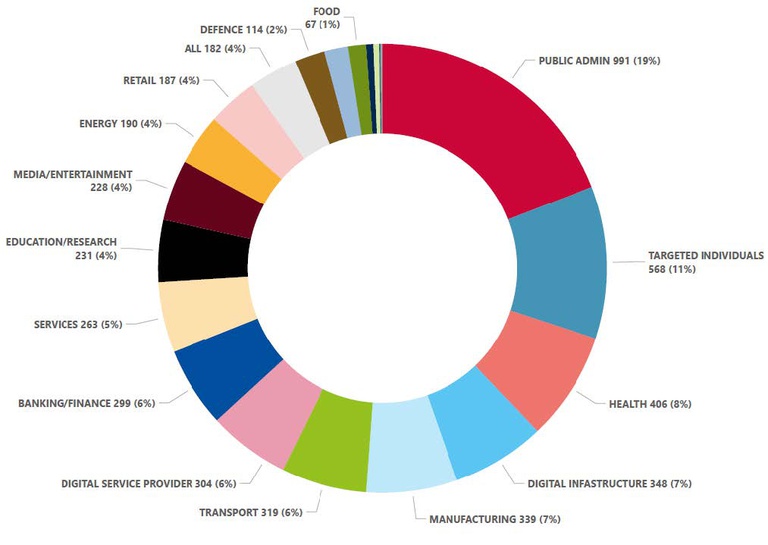
Sectors mostly targeted include public administrations for 19% and health for 8%. However, because of interdependencies, a cascading effect is observed, with a single event usually impacting several sectors at once. 6% of all events target the manufacturing, transport and finance sectors.
The ENISA Threat Landscape 2023 is the annual report of the EU Agency for Cybersecurity.
EU Agency for Cybersecurity Executive Director, Juhan Lepassaar stated that “Trust in the EU electoral process will critically depend on our capacity to rely on cybersecure infrastructures and on the integrity and availability of information. Now, it is up to us to ensure we take the necessary actions to achieve this sensitive yet essential goal for our democracies.”
Impact of social engineering & information manipulation campaigns
On total events related to social engineering, 30% targeted the general public, 18% public administration and 8% all sectors. Likewise, information manipulation campaigns targeted individuals for 47%, public administration for 29%, followed by the defence for 9% and media/entertainment for 8%. Information manipulation campaigns are considered to be a major threat to election processes.
Overview of evolving trends on threat actors
- Activities of threat actors such as cybercriminals, state-nexus actors, and hacktivists are influenced by geopolitical events. State-nexus actors increasingly target employees in key positions, politicians, government officials, journalists or activists. They mainly resort to traditional spear phishing e-mails and to social networks.
- Trojanising known software packages: we observe that state-nexus actors adopt attack patterns typically seen in criminal campaigns. Or, in some cases, state-nexus actors supported actions from cybercriminals whether directly or indirectly. Some of the techniques include targeted malvertising where malevolent sites point to trojanised versions of legitimate applications. Those actors also resort to techniques allowing them to have full control over the operating system (OS) boot process, and then making it possible to disable OS security mechanisms.
- Remote Monitoring and Management (RMM) software also stirred the attention of Cybercriminals. This software allows attackers to blend in with normal operations.
- Threat actors also exploit configuration errors in security products, in order to disable antivirus without administrator privileges or employing them for lateral movement.
- Cybercriminals turn to cloud infrastructure of potential victims to cause harm, primarily by abusing cloud misconfigurations. This is not limited to the organisations’ systems, storage and networks running in the cloud, but also extends to the management consoles of cloud infrastructures.
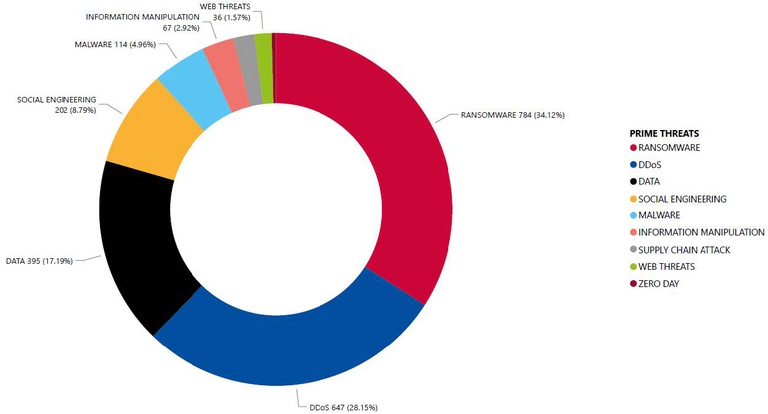
Prime Threats
Ransomware still gets top of the podium accounting for 34% of EU threats with DDoS, accounting for 28% of all threats.
Threats by sectors
Ransomware happens to target all sectors with manufacturing reaching 14% of all ransomware events, followed by health for 13%, then by public administration for 11% and services for 9%.
On DDoS attacks and data-related threats, 34% of the DDoS attacks targeted public administration, followed by the transport for 17%, and banking/finance sectors for 9%.
Threats against availability of internet affected primarily digital infrastructure for 28% and digital service providers for 10%.
The extent of the impact of supply chain attacks emerges as a substantial concern in relation to the upcoming elections. This is because such attacks affected public administration for 21% and digital service providers for 16%. Besides, exploitation of vulnerabilities was associated with events involving digital service providers for 25%, digital infrastructures for 23% and public administration for 15%.
Targeted sectors per number of incidents (July 2022-June 2023)
Financial gain and Disruption as top motivation
In most cases, top threats may be motivated by a combination of intentions such as financial gain, disruption, espionage, destruction or ideology in the case of hacktivism.
While ransomware attacks are primarily motivated by financial gain, a number of such attacks are also intended to have a disruptive effect. Disruption is now identified as the second most common motive after financial gain. Disruption is the key driver for DDoS attacks and for information manipulation.
Deep fake and AI
Artificial intelligence, and the complexity of Large Language Models (LLMs) received a lot of attention lately. Deepfakes and other such technologies can feed into the objective of realistic and targeted social engineering attacks. We need to be alerted to the potential misuse of artificial intelligence-powered chatbots in phishing attempts, information manipulation and cybercrime.
However, a number of older techniques require much less effort and still remain highly efficient and a resurgence of them has been observed. Search engine optimisation (SEO) poisoning and although dated, malvertising has sparked new interest amongst cybercrime actors.
Common Vulnerabilities and Exposures (CVE)
A grand total of 24,690 common vulnerabilities and exposures were recorded, marking an increase of 2,770 in comparison to the prior reporting period, which covered July 2021 to July 2022 and identified 21,920 vulnerabilities during that time.
Background
The ENISA Threat Landscape report maps the cyber threat landscape to help decision-makers, policy-makers and security specialists define strategies to defend citizens, organisations and cyberspace. This work is part of the EU Agency for Cybersecurity’s annual work programme to provide strategic intelligence to its stakeholders.
The report’s content is gathered from open sources such as media articles, expert opinions, intelligence reports, incident analysis and security research reports; as well as through interviews with members of the ENISA Cyber Threat Landscapes Working Group (CTL working group).
The analysis and views of the threat landscape by ENISA is meant to be industry and vendor neutral. Information based on OSINT (Open Source Intelligence) and the work of ENISA on Situational Awareness also helped document the analysis presented in the report.
Further Information
ENISA Health Threat Landscape 2023
ENISA Transport Threat Landscape 2023
Foreign Information Manipulation Interference (FIMI) and Cybersecurity Threat Landscape 2022
ENISA Threat Landscape Report 2022
ENISA Threat Landscape Supply Chain
Contact
For press questions and interviews, please contact press (at) enisa.europa.eu
Stay updated – subscribe to RSS feeds of both ENISA news items & press releases!
News items:
http://www.enisa.europa.eu/media/news-items/news-wires/RSS
PRs:
http://www.enisa.europa.eu/media/press-releases/press-releases/RSS





